HKEY_CURRENT_USERsoftwareMicrosoftInternet ExplorerMainStart Page Redirect=â€http://
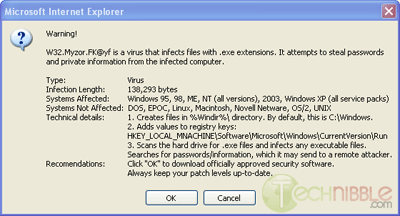
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionvirus name
HKEY_CURRENT_USERSoftwareMicrosoftWindows NTCurrentVersionWinlogon “Shell†= “%AppData%
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun ‘Random’ HKEY_LOCAL_MACHINESoftwareMicrosoftWindows NTCurrentVersionRandomIt can be generally considered to be able to execute dreadful workout on the traded off framework and to boost complete access over the actual victim PC
No comments:
Post a Comment